More than 11% of the websites using the secure version of HTTP (HTTPs) appear to have a vulnerability.
Behind this alarmist title, there is indeed a very common error. The french Start-up DareBoost, specialized in automated website testing, investigated on a specific security issue: the Mixed Content. According to this study, 1 199 out of 10 511 secure websites present this problem (11.4%).
HTTPS and Mixed Content in a few words
The HTTPS protocol
Mixed content can be found in HTTPS pages (which stands for HTTP Secure, a coded version of the communication between the user and the website, used for instance in banking transactions).
The secure version of HTTP is used to prevent from attacks, like the “Man In The Middle” one.
As it is encrypted, the communication is protected from eavesdropping.
The objective of HTTPS is to ensure the confidentiality and the integrity of the exchanged data.
Mixed Content
On a web browser, the use of HTTPS is very commonly represented with a padlock. The thing is, pages are composed of various resources, and sometimes some of them are loaded without using the secure protocol.
This is what we call Mixed Content: an HTTPS page, which includes HTTP content. And this can question the security of the communication.
The error is not rare, you probably have already seen it, perhaps without paying attention.
To illustrate this, here are two screenshots, from the latest version of Firefox, on the same HTTPS website.
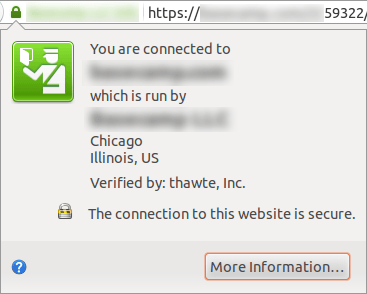
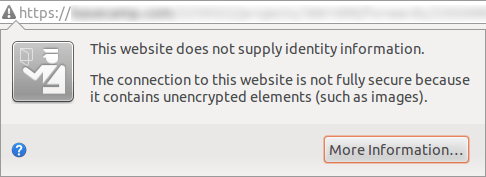
We notice here the presence of the padlock. When clicking on it, the user gets access to information regarding the website identity.

Still on the same website, but after detection, by the browser, of mixed content in another page. A warning icon takes the place of the padlock. The website identity information is replaced by a message warning the user of a security issue.
Is it a serious matter?
There are actually two types of mixed content: active and passive.
Passive mixed content is different from active, because it only presents minor risks. An attacker would not be able to damage the integrity of the whole web page received by a user, but he still could modify some content, like an image. In some cases, there is a possibility of identity theft for the user, in his communication with the server.
Concerning active mixed content, the risk is higher, like theft of sensitive data.
(To know more about this:
https://blog.mozilla.org/tanvi/2013/04/10/mixed-content-blocking-enabled-in-firefox-23/)
There is a real possibility of attack. However, we have to remain rational : they are not the most frequent, and the risk has to be considered regarding the level of sensitivity of the exchanged data.
Although, as seen above, this error sends a negative image to the user, with the loss of the security indicator, and the appearance of a warning. For the website, this may be very problematic : indeed, once the warning has appeared, it is maintained throughout all the browsing on the site, even if the next visited page does not contain any issue.
The web browsers come to help
As we have seen above, the browser tells the user when he is dealing with Mixed Content, but maybe the way he does in not enough known.
Firefox, Chrome and Internet Explorer (in their current versions) block Active Mixed Content, totally or partially.
This way, the impact of the security flaw linked to the mixed content is limited, thanks to the work of the web browsers.
A problem remains : the content blocked this way is not rarely useless, and the fact that they are not requested can lead to a damaged user experience. It is then imperative, for the website administrators, to rectify these errors.
Until now, Google Chrome still let some of the Active Mixed Content pass through. It may adopt a stricter policy in its version 36.0 (source https://twitter.com/igrigorik/status/461572780564045824).
This page (https://www.ssllabs.com/ssltest/viewMyClient.html) allows you to test your web browser behavior regarding Mixed Content.
What about your website?
www.dareboost.com is an automated testing tool to check web performance and quality. It allows you to check if a page contains Mixed Content (you only have to enter the address of the HTTPS page you want to analyze, and to submit the form. The test is free for homepages).
Methodology
Based on data offered by Httparchive.org project, DareBoost has identified, among ~300 000 websites, those using HTTPS on their homepages. The start-up isolated the 10511 results obtained, then found the websites which used non-secure HTTP requests (Mixed Content cases).
NB: redirected resources (301 & 302 HTTP codes) have been excluded for technical purposes, though they might be considered as Mixed Content issues.
You should also be warned that data are collected by httparchive using Internet Explorer 9, that blocks XMLHttpRequest Mixed Content and does not support WebSockets. It may also have limited the number of websites detected as having this vulnerability.

One thought on “Vulnerability on more than 11% of secure websites”
Comments are closed.