Cookies are widely used throughout the Web because they allow publishers to store data directly on the user’s Web browser. They’re particularly used to identify the user’s session, allowing the web server to recognize the user as they navigate through the site, and generally contain sensitive data. You have to properly protect them.

The Set-Cookie HTTP header
A small reminder: each time a server responds to a request, the HTTP response may contain a Set-Cookie instruction (as an HTTP header) requesting the web browser to create one or more cookies associated to one or more domains. Those cookies store information that will be transmitted in future requests on these domains.
Here is the syntax of such a header:
Set-Cookie: <name>=<value>[; <Max-Age>=<age>] [; expires=<date>][; domain=<domain_name>] [; path=<some_path>][; secure][; HttpOnly]
Every cookie is identified by its name and store a value. A lifetime (max-age) or an expiry date can be defined, to limit data retention over time. Note that if both attributes are set then the lifetime value (max-age) will prevail.
By default, a cookie is always associated with the location of the current document (domain as well as path) but the Set-Cookie header allows to define custom values to restrict or extend paths to which the cookie will be sent (for example, if a domain is specified, subdomains will be included). Consequently, one of the best practices regarding the security of cookies is to properly manage their scopes.
The last 2 attributes, secure and HttpOnly specifically deal with security. Please note that they do not require any associated value: their very presence is enough for the browser to behave as expected when it comes to the cookie.
Prevent the use of a cookie on the client side with HttpOnly
A cookie can be set and used over HTTP (communication between a web server and a web browser), but also directly on the web browser via JavaScript.
In an XSS breach case, an attacker could inject malicious Javascript on the page, and potentially access to the cookies that, as a reminder, often contain sensitive information. Needless to say that a website should not have XSS breaches, it’s a major security issue. But it’s hardly possible to make sur to never have one (Content Security Policy can be an additional way to protect your visitor from the exploitation of an XSS attack).
The “HttpOnly” flag blocks the access of the related cookie from the client-side (it can’t be used from Javascript code): if an attacker was to succeed in injecting some javascript despite all your precautions, he won’t be able to access the cookies anyway. That will significantly limit the attack range.
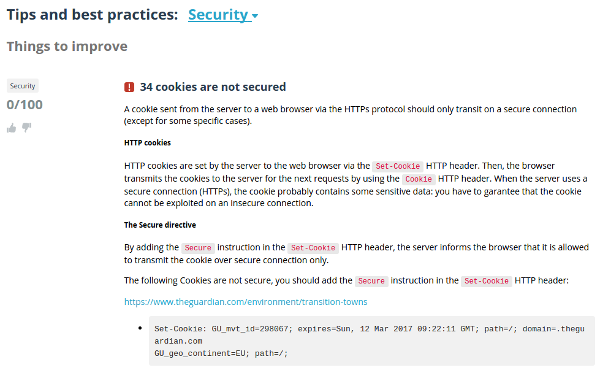
Forbid to use a cookie without HTTPs thanks to the Secure flag
We regularly recommend it on this blog: your website should use HTTPs. If you have already adopted this protocol and applied our previous advice, you may think that your cookies are protected as they can only be transmitted through a secure communication, and neither they can be access throught Javascript (thanks to HttpOnly flag). Unfortunately, a significant issue remains.
What if a user comes to your website via HTTP, for example because he’s typing your URL without mentioning “https://”? This could also happen if your web page contains mixed content.
Setting an HTTP Strict Transport Security (HSTS) header, that will enforce HTTPS usage, will limit the risks for all the upcoming visits, but not for the first one. And all the browsers do not support this header…
Actually, only the Secure attribute will let you forbid a cookie to be ever transmitted over simple HTTP.
The interest of this flag is clearly mentioned in the RFC HTTP State Management Mechanism:
Servers that require a higher level of security SHOULD use the Cookie and Set-Cookie headers only over a secure channel. When using cookies over a secure channel, servers SHOULD set the Secure attribute (see Section 4.1.2.5) for every cookie. If a server does not set the Secure attribute, the protection provided by the secure channel will be largely moot.
Obviously, keep in mind that a cookie using this secure flag won’t be sent in any case on the HTTP version of your website. So be careful if your website still has got both HTTPS and HTTP areas.
Our web page analysis tool will let you ensure at a glance that all of your cookies are secured, by checking if HttpOnly and Secure are properly used!